All articles
Passphrases and hidden wallets
TABLE OF CONTENTS
- Passphrase basics
- Important characteristics of passphrases
- How does it work?
- Choosing a passphrase
- Disabling / re-enabling the passphrase feature
- Passphrase FAQs
Passphrase basics
- A passphrase functions like an extra word added to your recovery seed
- Using your recovery seed alone grants access to your Standard wallet
- Each unique combination of 'recovery seed + passphrase' grants access to a corresponding unique Hidden wallet
- You must remember your passphrase, as it is never stored on your Trezor device! If you forget a passphrase, then you will not have access to the associated funds
Only use a passphrase once you understand how it works. Funds secured by a passphrase can't be recovered without it!
Important characteristics of passphrases
- Passphrases are not stored anywhere on the device.
- It is only used temporarily whenever you enter it.
- A passphrase, as implemented in Trezor devices, can be any character or set of characters, a word, or a sentence up to 50 bytes long (~50 ASCII characters).
- Characters from the extended ASCII character set cannot be entered using the Trezor device itself. If you create a passphrase including characters from the extended ASCII character set - i.e., decimal 128 (€) to 255 (ÿ) - these can only be entered when using Trezor Suite on a trusted computer.
- Moreover, these characters may not be rendered correctly on the Trezor display.
- Passphrases are case-sensitive. Lowercase and uppercase characters are distinguished and count as different.
- A space (blank) is a valid character.
- The passphrase and recovery seed belong together. Neither can be used without the other if you sent your coins to a passphrase-protected hidden wallet.
Passphrases can't be hacked, as they're not stored on the device
Each passphrase creates a new hidden wallet, so always check you're entering the passphrase correctly
A strong passphrase means your coins are (extra) safe
Each passphrase creates a new hidden wallet, so always check you're entering the passphrase correctly
A strong passphrase means your coins are (extra) safe
How does it work?
As part of the initialization process, your Trezor device generates a random number which is converted into a recovery seed and stored in the memory. Your Trezor uses this string of standard English words to generate your private keys, serving as a kind of 'master access key' for unlocking access to your Bitcoin funds.By default, the Trezor Model One creates a wallet with a 24-word seed phrase, whereas the Trezor Model T generates a wallet using a 12-word seed. This is referred to as your 'Standard wallet' in Trezor Suite.
By using a passphrase, you're effectively adding an extra word to the seed phrase, creating a brand new 'Hidden wallet'.
In fact, you can generate as many passphrase-protected hidden wallets as you like, but you must be extremely careful not to lose any of your passphrases. Remember, if you lose a passphrase, you lose access to any funds stored in the hidden wallet!
Essentially, whenever a Trezor device is used, it derives a cryptocurrency wallet using the following (extremely simplified) formula:
recovery seed + passphrase = hidden wallet
which can be summarized using the following schematic:
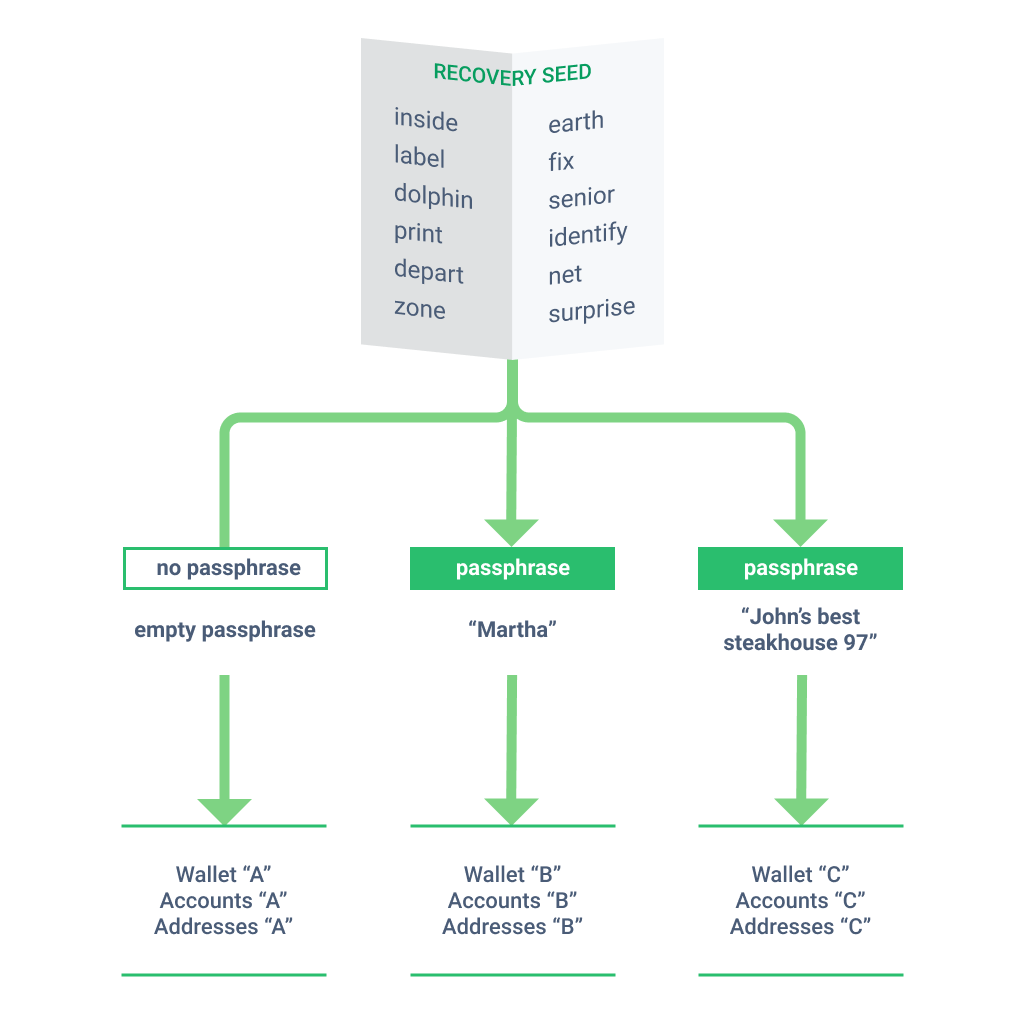
In this schematic, Wallet "A" corresponds to the Standard wallet, whereas "Wallet B" and "Wallet C" correspond to two unique passphrase-protected Hidden wallets.
Every time you access Trezor Suite, the Select wallet type modal window appears:
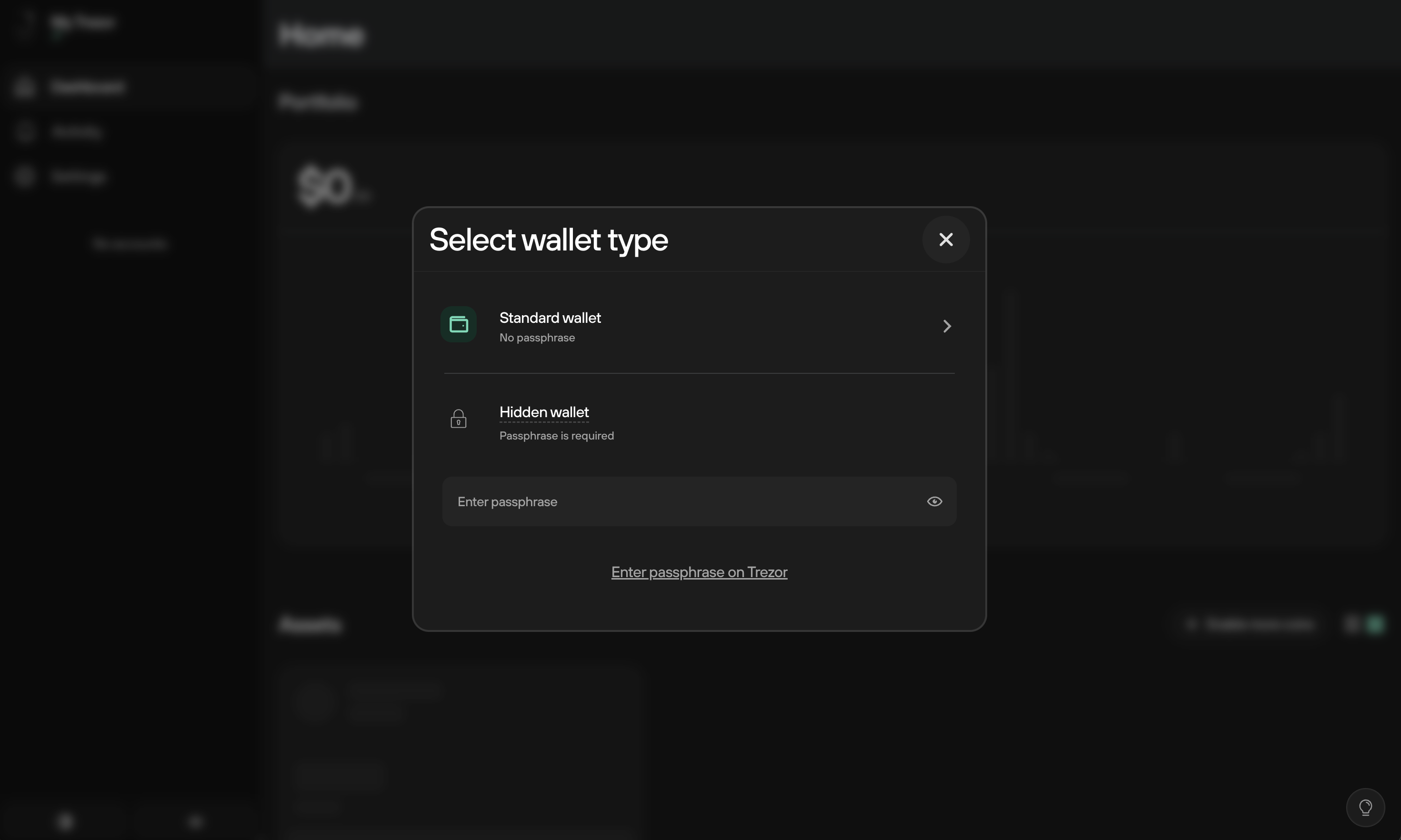
- Click on Standard wallet to access your 'primary' set of accounts, which are not passphrase protected
- Alternatively, enter your memorable passphrase to access a Hidden wallet or create a brand new Hidden wallet
Passphrases are used to create unique Hidden wallets and control access to them, without requiring a second hardware wallet or recovery seed. This means your funds are safe, even if your recovery seed is compromised.
Choosing a passphrase
Whereas your recovery seed is randomly generated, you choose your own passphrase:
- It can be any memorable word / phrase / sentence up to 50 bytes (about 50 ASCII characters)
- It is case sensitive i.e. "Hello World" is not the same as "Hello world"
- Spaces are valid characters - every character matters
- An empty passphrase is the same as 'seed-only' access to your Standard Wallet
To access a Hidden wallet, you must enter the passphrase with 100% accuracy
If you enter anything else, a brand new Hidden Wallet will be created
If you forget your passphrase, your hidden wallet is irretrievable
If you enter anything else, a brand new Hidden Wallet will be created
If you forget your passphrase, your hidden wallet is irretrievable
Disabling / re-enabling the passphrase feature
The passphrase feature is enabled by default. This means that after initializing your device, whenever you access Trezor Suite you will see the 'Select wallet type' modal window (see above).
However, if for any reason you do not wish to access or create hidden wallets, the passphrase feature can be toggled off or on via the Device settings page in Trezor Suite:
- First, connect your Trezor and unlock it using your PIN.
- Once connected and unlocked, you will see the Dashboard view in Trezor Suite.
- You must then access the device Settings by clicking on the 'gear' icon located in the top right-hand corner.
- Under the Device settings menu, scroll down to the Security section and simply click the toggle switch in the Passphrase section:
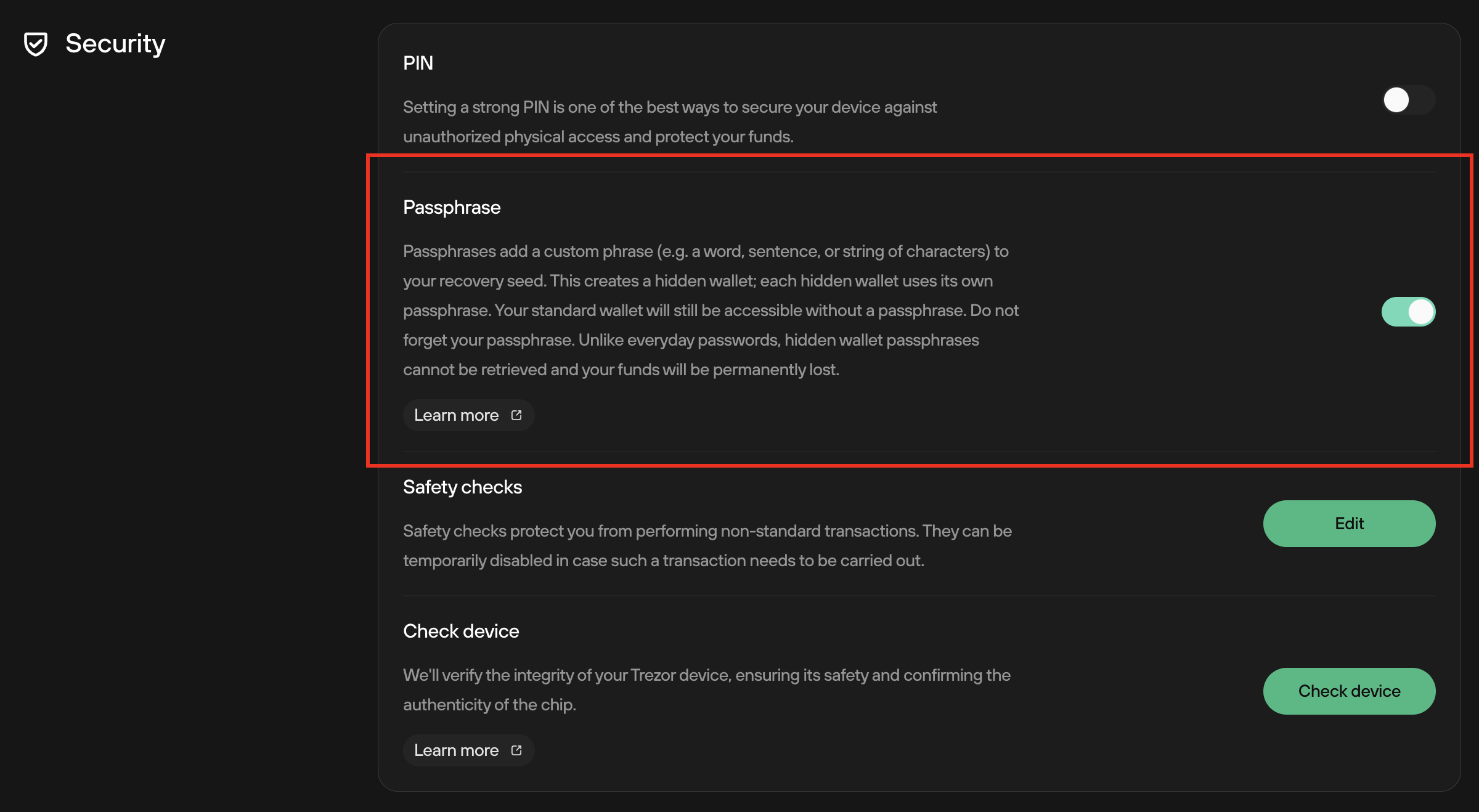
- Follow the instructions displayed on your Trezor device, to Confirm that you really want to disable / enable passphrase protection
- Once confirmed, you will see a 'Settings changed successfully' pop-up notification in the top-right hand corner of Trezor Suite
Using passphrase in other apps
By using the same combination of recovery seed and passphrase, the same wallet with identical addresses is derived - no matter which application is used:Passphrase FAQs
I've lost my Trezor! Can I recover a passphrase protected wallet?First, there’s no need to panic. You can use a second Trezor device to recover your existing accounts using the recovery seed.
You can enable the passphrase feature straight away, and once your Recovery Seed is loaded onto your device, just enter the exact same passphrase you created for the hidden wallet.
What are the benefits of using the passphrase feature?
A passphrase protects your Recovery Seed and is not stored anywhere, meaning if someone compromised your Recovery Seed, they would not be able to access your accounts – unless they also knew each passphrase.
You can create any number of new passphrases and associated wallets. This means you can redistribute balances for added security, or simply to help you organize your accounts.
What are the risks of using the passphrase feature?
Please take all necessary precautions in order to preserve your passphrase(s) for future reference
If you forget a passphrase, you lose access to any associated funds!
Extra info
"Passphrase - the Ultimate Protection for Your Accounts" on the Trezor Blog