What is U2F?
Universal 2nd Factor (U2F) is an open authentication standard that strengthens and simplifies two-factor authentication (2FA) by using specialized USB or NFC devices based on a similar security technology found in smart cards. While initially developed by Google and Yubico, with a contribution from NXP Semiconductors, the standard is now hosted by the FIDO Alliance. The safe characteristics of asymmetric cryptography fall into the security philosophy of Trezor. With U2F support in Trezor, it is possible to secure accounts and identities online.
Benefits of U2F
- Private keys are never sent via the internet
- Confidential information is never shared thanks to public key cryptography.
- Easier to use than traditional 2 factor authentication.
- No retyping of one-time codes involved.
- No personal information shared with private key.
While a backup is theoretically easier, it is not possible for all U2F keys. When using U2F there is no secret shared and no confidential databases stored by the provider, a hacker cannot simply steal the entire databases to get access. Instead, he has to target individual users, which is much more costly and time-consuming. Moreover, it is possible to back up a secret (private key).
How does it work?
When logging into a website, the user generally authenticates himself by providing a username and a password. With Trezor and U2F, the user will have to additionally confirm the login with a click of the button on the Trezor device.
Trezor always uses a unique signature for each and every user account registered.
- Trezor requires the user to back up the recovery seed during the initial setup of the device. This is a one-time process for all functions of the device. The recovery seed represents all the private keys generated by the device and can be used to restore the linked wallet at any time.
- Allows for an unlimited number of U2F identities, which are all saved under one backup.
- The recovery seed is safely stored inside Trezor. It will never be shared, as it can never leave the device. No viruses or hackers can access it.
- Phishing protection with on-screen verification. Trezor always displays the URL of the website the user wants to log in to, and what exactly is going to be authorized; therefore it is possible to verify what was sent to the device is the same as what was expected.
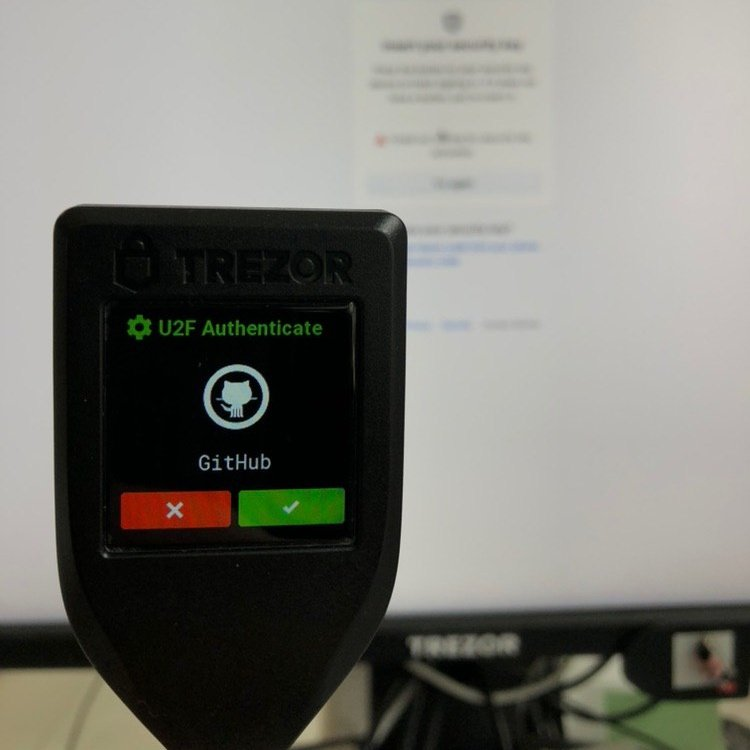
Trezor with U2F
To boost your online security, Trezor can serve as a hardware security token for U2F, but with backup/recovery functions and convenience. You can start using Trezor as your second-factor authentication token with services such as Google, GitHub or Dropbox. A further advantage of Trezor is that its users can truly verify what they are about to authorize on the device display.
In this short tutorial, we will show you how to enable Two-Factor Authentication on a Google account and register a Trezor device as a U2F authentication token.
1. Visit Google.com and sign in to your account

2. Access the "Security" settings and enable "2-Step Verification"
After accessing your Google account, navigate to the security settings on the left of the page. You will see an option to enable 2-Step Verification. When this feature is enabled, your Google account requires a second verification in addition to your standard password.
Click on 2-Step Verification and then GET STARTED to continue.
3. Select "Security Key" out of other options used to sign in
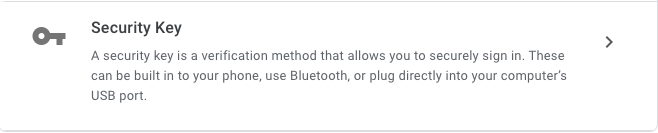
Google will ask you to sign in to your account again. This is a security precaution to ensure you are the one changing your settings. When signing in, Google asks you to select the preferred Method of 2-Step Verification. Google will offer their native solution, but you have much better solution, your Trezor device. Therefore, click on Choose another option and select Security Key
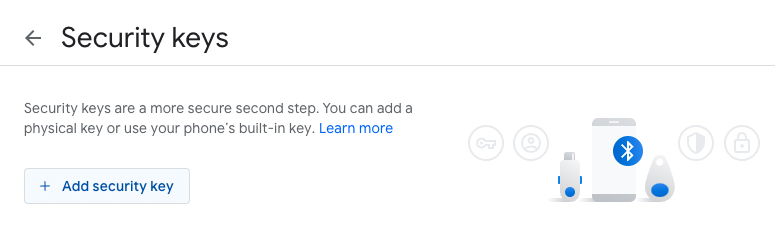
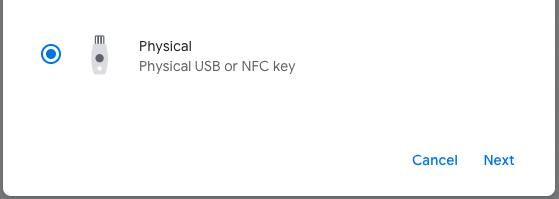
4. Connect your Trezor device and register it as a U2F security key for this service

5. Name your security token
Here you select the name Google sees when you use your device. This name is not the same as the name you chose when you first initialized your device.
6. Enjoy!
Next time you sign in to your Google account, you will be asked to confirm the login on your device.
U2F Support
U2F is enabled in Chrome/Chromium browsers out of the box
In Firefox you need to enable U2F manually:
Type about:config into the Firefox address bar and press Enter
Search for u2f
Double-click on security.webauth.u2f to enable U2F (or right-click and select Toggle)
Restoring U2F Counter on Trezor
Restoring a seed on another Trezor (see the dedicated recovery pages for the Trezor Model One and Trezor Model T) restores all the U2F keys too, since they are derived from one master key. Due to the design of U2F, some services might implement a counter that records the number of sign-ins. However, if you have firmware version 1.4.2 or higher, the U2F counter is restored automatically.
How to add U2F to sudo command
1. Open up the sudo configuration file:
2. Add this at the end of the file:
auth required pam_u2f.so authfile=/etc/u2f_mappings cue
Test your configuration by opening up another terminal window and running a sudo command. If these things are done correctly, you will be asked for your password and then prompted to “Please touch the device.” Your Trezor device will also be prompting you to authorize the request. Congratulations, your system now requires your Trezor to run sudo.